Update( May 28 2015)
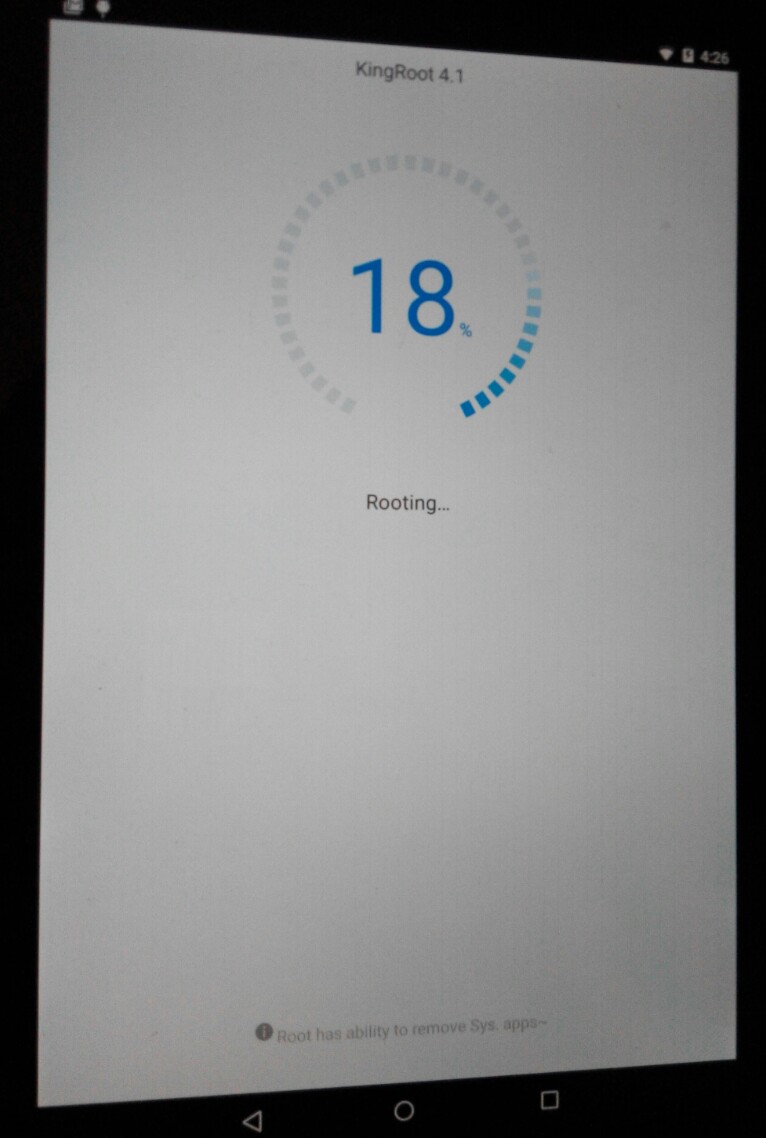
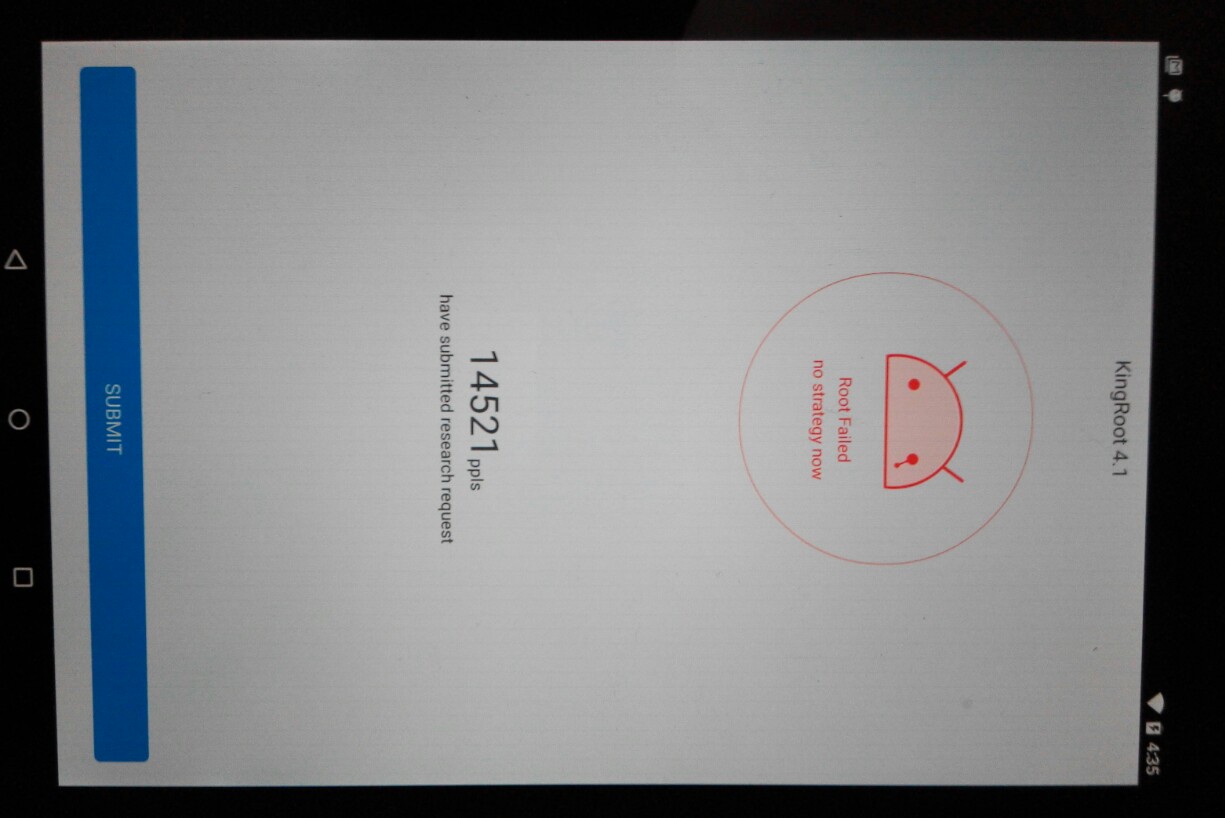
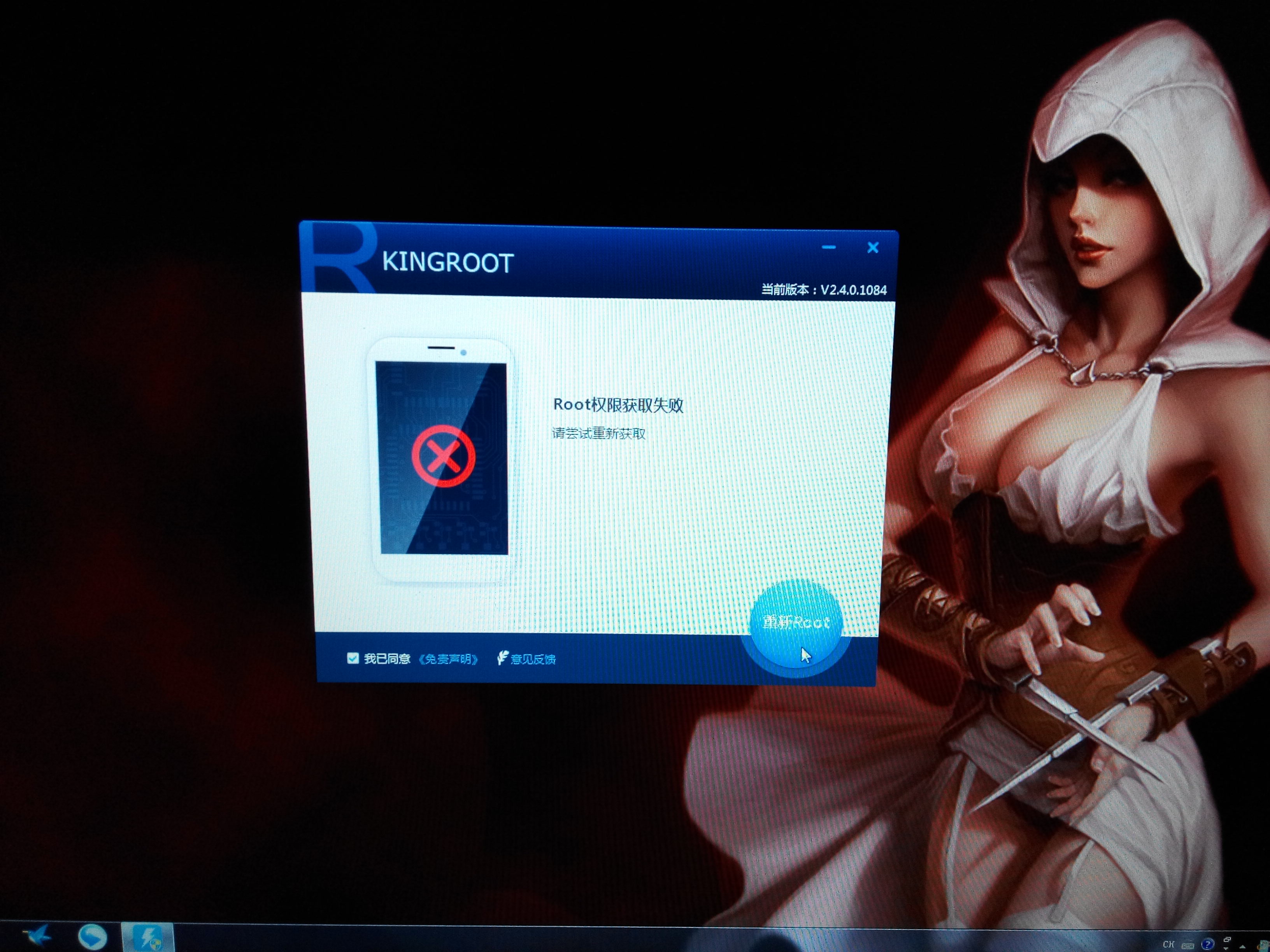
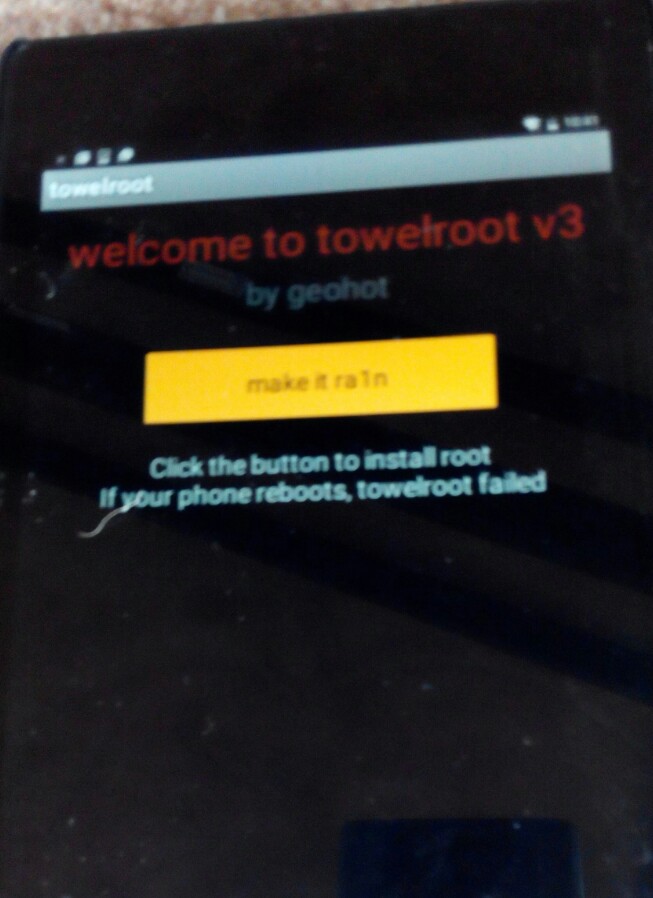
The porting work of the PaX patch already done. We tested it with Towel & KINGROOT. The result as expected: they all failed to root the Android 5.0.2 with kernel code base from 2014. Perhaps, we might try to make GRSEC & RBAC into the Android in the future………
armv7-nexus7-grsec
PaX/Grsecurity patch for Nexus7, which the original version is 3.4 kernel based with a bunch of backport features and fixes. In some particular cases, TrustZone is useless if the Android kernel were compromised. I don't think we need another rootkit-friendly solution like SELinux always does. Get rid of one entire class of vulns in kernel would be an inevitable ways to make your device secure.
Credit for PaX/Grsecurity
PaX/Grsecurity is the most respected 0ld sch00l community and they have been creating the best defense-in-depth kernel hardening solution for 14 years. What PaX/Grsecurity brings to us, is amazing and incridble work. Unfortunately, there are a lot of reasons that PaX/Grsecurity don't get the credit what they deserves. Let me make this short: To love those who are hatred by BIG BROTHER. That's the fuc*ing point.
What makes us ticks
The age of IoT( Internet of things) is coming soon…There will be huge numbers of devices running with diverse communication protocols. For the simply classify, I'll only treat these devices as two types: One with TCP/IP stack, or not. The one with TCP/IP stack might have high probablity run with GNU/Linux. The one without TCP/IP stack may be just a simple MCU stuff. The heterougenous network need to be protected in various ways. These devices may be running on our cars, refrigrator, or everywhere around us, which could be a risk to our money-shitty property and even lives. That’s one of most important reasons we need to "H A R D E N E N I N G E V E R Y T H I N G" by free software.
PaX/Grsecurity
| NAME | DESCRIPTION | AUTHORS |
|---|---|---|
| PAGEEXEC | paging based non-executable pages | The PaX team, Mar 15 2003 |
| SEGMEXEC | segmentation based non-executable pages | The PaX team, May 1 2003 |
| ASLR | address space layout randomization | The PaX team, Mar 15 2003 |
| MPROTECT | mmap() and mprotect() restrictions | The PaX team, Nov 4 2003 |
| RANDUSTACK | userland stack randomization | The PaX team, Feb 12 2003 |
| RANDKSTACK | kernel stack randomization | The PaX team, Jan 24 2003 |
| RANDMMAP | mmap() randomization | The PaX team, Jan 24 2003 |
| RANDEXEC | non-relocatable executable file randomization | The PaX team, Feb 19 2003 |
| VMMIRROR | vma mirroring, the core of SEGMEXEC and RANDEXEC | The PaX team, Oct 6 2003 |
| EMUTRAMP | gcc nested function and kernel sigreturn trampolines emulation | The PaX team, May 1 2003 |
| EMUSIGRT | automatic kernel sigreturn trampoline emulation | The PaX team, Feb 19 2003 |
| UDEREF | Prevent improper userland code/date access by the kernel | The PaX team, May 15 2007 |
PaX/Grsecurity writings
intro | Dec 30 2010
Assorted Notes on Defense and Exploitation | Dec 31 2010
False Boundaries and Arbitrary Code Execution | Jan 2 2011
The Dangers of Copy and Paste | Feb 1 2011
The Unseen Benefits of a Security Mindset | Mar 12 2011
Much Ado About Nothing: A Response in Text and Code | Apr 16 2011
Recent Advances: How We Learn From Exploits | Feb 15 2012
Supervisor Mode Access Prevention | Sep 7 2012
Inside the Size Overflow Plugin | Aug 28 2012
Recent ARM Security Improvements | Feb 18 2013
KASLR: An Exercise in Cargo Cult Security | Mar 20 2013
Guest Blog by Rodrigo Branco: PAX_REFCOUNT Documentation | Mar 21 2015
GCC plugins
Better kernels with GCC plugins
History
2005
grsecurity 2.1.0 and kernel vulnerabilities
the “Turing Attack” (was: Sabotaged PaXtest)
2009
2010
Brad Spengler (PaX Team/grsecurity) interview
2011
proactive defense: using read-only memory
2012
Why are the grsecurity patches not included in the Vanilla Kernel?
2013
How The Linux Foundation and Fedora are Addressing Workstation Security
2014
Some Links for Newbies on Grsecurity, and the Big Picture
How GNU/Linux distros deal with offset2lib attack?